Access control
Access control solutions are used to manage the entry, exit and presence of people in a building, on a site or in a restricted area. These systems are put in place for security, to control the number of people in a space, confidentiality, resource management and also combined with time and attendance management.
Our new solutions for access management, access control :
ZBioCVSecurity : Access control with visitor module
Visitor access and management
CVSecurity provides a complete Web security platform with hybrid biometrics adoption and computer vision technology. It contains several modules:Read more
Close
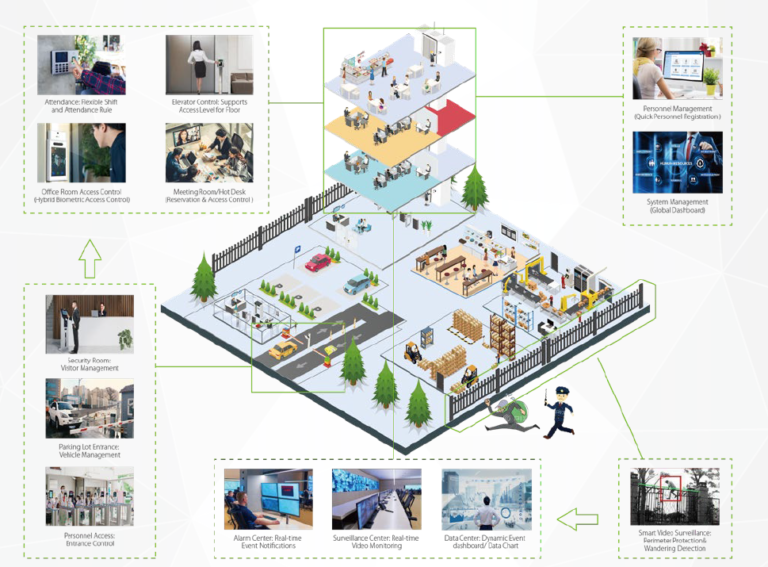
 Personnel, Time and attendance, Access control, Visitor, gestion, parking, elevator control, Face Kiosk, video management, guard patrol, intelligent video analysis, locker management, intruder alarm, service center and other other intelligent subsystems.
Personnel, Time and attendance, Access control, Visitor, gestion, parking, elevator control, Face Kiosk, video management, guard patrol, intelligent video analysis, locker management, intruder alarm, service center and other other intelligent subsystems.
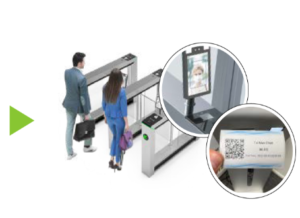
- Taking photos of visitors
- Supports automatic logout of visitor account. When a visitor does not exit normally, the system will retain the data. When the visitor’s visit expires, the system will automatically reset the visitor’s data.
- Individualized access control for each visitor, with access to defined areas, elevator floors, etc.
- Various authentication methods such as facial recognition, fingerprints, biometric cards, passwords and QR codes.
- Check visitor’s last location, history and timed pop-ups or unregistered visitors.
Complete hardware + software access management solution
Read more
Close
 This approach begins with the precise identification of users and their roles within the system. Each individual is assigned access rights according to his or her responsibilities, thus ensuring an appropriate distribution of permissions.
Implementing comprehensive access management also involves continuous monitoring of user activities. Monitoring tools are deployed to detect any anomaly or suspicious activity, enabling rapid reaction in the event of a potential threat.
At the same time, access management needs to be agile and scalable. Authorizations can be adjusted in real time to reflect organizational changes, promotions or employee departures, ensuring constant security.
ask for the doc => https://horomeca.com/contact/
This approach begins with the precise identification of users and their roles within the system. Each individual is assigned access rights according to his or her responsibilities, thus ensuring an appropriate distribution of permissions.
Implementing comprehensive access management also involves continuous monitoring of user activities. Monitoring tools are deployed to detect any anomaly or suspicious activity, enabling rapid reaction in the event of a potential threat.
At the same time, access management needs to be agile and scalable. Authorizations can be adjusted in real time to reflect organizational changes, promotions or employee departures, ensuring constant security.
ask for the doc => https://horomeca.com/contact/Atlas Bio series controller
- Web-based integrated management application
- Advanced access control
- Supports ZKTeco fingerprint readers with Wiegand, RS485 or OSDP v2.1.7 communication protocols (updated Nov. 2022)
- Compatible with KR610 and KR620
- 1, 2 or 4-door management models
Read more
Close
The Atlas series combines the latest generation of 1, 2 and 4-door biometric access control panels with an integrated web application that eliminates the need for management software.
The Atlas series supports any third-party reader that communicates with Wiegand, RS485 or OSDP v2.1.7 communication protocols (updated Nov. 2022).
Complete, user-friendly management from anywhere via the Internet.
All your doors are secured with WiFi devices that can each control up to several doors.
Our access control systems can be equipped with badge readers, RFID, MiFare or HID, fingerprint readers and facial recognition.
Easy to use, the integrated web application gets you up and running quickly.
Firmware can be upgraded to keep your system up to date with the latest features and security enhancements.
Synergy Acces software or
Access module in Synergy WF
Scalable security solutions and access control management for your organization,
Synergy Access is a scalable access control solution – for securing and controlling access to your organization, with total control over access points on your premises.
Read more
Close
This solution is also available as an add-on module to Synel’s Synergy Workforce –(https://horomeca.com/logiciel-de-pointage/) with time & attendance and other personnel management modules – or as a completely stand-alone access control system.
The benefits? Hosting your access control solutions in the cloud – so you don’t have to worry about server management, simple upgrades, automatic solution updates, and the highest levels of data security.
Control access points with security groups and time zones, your company can create specific security groups to control user access to specific doors. The added benefit of defining time zones allows you to control the days and times when users can access your premises, reinforcing your security.
Synergy Access allows you to create an unlimited number of security groups, and users can be members of several access control groups.
QR600
- Robust, waterproof metal case
- Integrated keyboard (QR600-HK and QR600-VK models)
- IP65 certification
- Compatible with dynamic QR code solutions
- Supported codes: QR Code, PDF417, Data Matrix, MicroPDF417, Aztec
- Communications: Wiegand and RS485
- 125 kHz
- IC 13.56 MHz (including Ultralight)
- Mifare (S50 / S70)
- CPU, NFC (analog card), Desfire EV1, NTag
Bio Entry
The BioEntry is a high-tech biometric reader, widely used throughout the world.
It is compatible with a wide range of software solutions for access control, time & attendance and time & attendance management.
It supports several reading technologies: Proximity EM, HID Prox, Mifare, Felica, NFC, Desfire and iClass.
IP67-certified, it is fully protected against humidity, dust and liquids.
IK08-certified, it is vandal-resistant.
Thanks to its sturdiness, it is perfectly suited to securing building entrances.
 Access control is an essential element of security in many environments, from buildings to computer networks and sensitive information systems. It refers to measures taken to regulate and monitor the entry and exit of people, vehicles or data in a given space or system.
In the context of buildings, access control aims to protect installations and occupants from unauthorized intrusion. It can take the form of physical devices such as locks, card readers or biometric recognition systems. These measures make it possible to restrict access to specific areas, track people’s movements and ensure that only authorized people can enter sensitive areas.
Building access control is an essential aspect of security and facility protection. This is a set of measures and devices put in place to regulate and monitor the entry and exit of people in a given space, ensuring that only authorized persons can access sensitive areas.
Building access control systems can take many forms. One of the most commonly used means is the installation of locks and keys, which restrict access to specific doors and areas. However, these traditional systems have evolved to include more advanced technologies such as access cards, PIN codes and biometric recognition systems.
Access cards are electronic devices assigned to authorized individuals. They can be programmed to provide different levels of access according to each person’s specific needs. PIN codes are personal numerical combinations that must be entered on a keypad to open a door. Biometric recognition systems, on the other hand, use unique physical characteristics such as fingerprints, facial recognition or iris recognition to identify individuals and grant them access.
In addition to these devices, access control systems can also be equipped with surveillance cameras, motion sensors and intercom systems. These additional components enhance security by enabling real-time monitoring, intrusion detection and communication between people inside and outside the building.
The advantages of building access control are numerous. Firstly, it prevents unauthorized intrusion by restricting access to sensitive areas. This ensures that only authorized persons, such as employees, residents or pre-registered visitors, can enter the building.
What’s more, by keeping a record of entries and exits, access control systems can provide valuable information for security management, identifying who is in the building at any given time.
Building access control is particularly important in sensitive environments such as companies, government institutions, hospitals or data centers. In these contexts, protecting assets, confidential information and people is an absolute priority.
In conclusion, building access control is an effective way of enhancing the security and protection of facilities. Through a combination of physical devices and advanced technologies, it regulates access to sensitive areas, prevents unauthorized intrusion and provides valuable information for security management.
What is access control? It is in fact this
Access control is an essential element of security in many environments, from buildings to computer networks and sensitive information systems. It refers to measures taken to regulate and monitor the entry and exit of people, vehicles or data in a given space or system.
In the context of buildings, access control aims to protect installations and occupants from unauthorized intrusion. It can take the form of physical devices such as locks, card readers or biometric recognition systems. These measures make it possible to restrict access to specific areas, track people’s movements and ensure that only authorized people can enter sensitive areas.
Building access control is an essential aspect of security and facility protection. This is a set of measures and devices put in place to regulate and monitor the entry and exit of people in a given space, ensuring that only authorized persons can access sensitive areas.
Building access control systems can take many forms. One of the most commonly used means is the installation of locks and keys, which restrict access to specific doors and areas. However, these traditional systems have evolved to include more advanced technologies such as access cards, PIN codes and biometric recognition systems.
Access cards are electronic devices assigned to authorized individuals. They can be programmed to provide different levels of access according to each person’s specific needs. PIN codes are personal numerical combinations that must be entered on a keypad to open a door. Biometric recognition systems, on the other hand, use unique physical characteristics such as fingerprints, facial recognition or iris recognition to identify individuals and grant them access.
In addition to these devices, access control systems can also be equipped with surveillance cameras, motion sensors and intercom systems. These additional components enhance security by enabling real-time monitoring, intrusion detection and communication between people inside and outside the building.
The advantages of building access control are numerous. Firstly, it prevents unauthorized intrusion by restricting access to sensitive areas. This ensures that only authorized persons, such as employees, residents or pre-registered visitors, can enter the building.
What’s more, by keeping a record of entries and exits, access control systems can provide valuable information for security management, identifying who is in the building at any given time.
Building access control is particularly important in sensitive environments such as companies, government institutions, hospitals or data centers. In these contexts, protecting assets, confidential information and people is an absolute priority.
In conclusion, building access control is an effective way of enhancing the security and protection of facilities. Through a combination of physical devices and advanced technologies, it regulates access to sensitive areas, prevents unauthorized intrusion and provides valuable information for security management.
What is access control? It is in fact this Access control is an essential element of security in many environments, from buildings to computer networks and sensitive information systems. It refers to measures taken to regulate and monitor the entry and exit of people, vehicles or data in a given space or system.
In the context of buildings, access control aims to protect installations and occupants from unauthorized intrusion. It can take the form of physical devices such as locks, card readers or biometric recognition systems. These measures make it possible to restrict access to specific areas, track people’s movements and ensure that only authorized people can enter sensitive areas.
Building access control is an essential aspect of security and facility protection. This is a set of measures and devices put in place to regulate and monitor the entry and exit of people in a given space, ensuring that only authorized persons can access sensitive areas.
Read more
Close
Building access control systems can take many forms. One of the most commonly used means is the installation of locks and keys, which restrict access to specific doors and areas. However, these traditional systems have evolved to include more advanced technologies such as access cards, PIN codes and biometric recognition systems.
Access cards are electronic devices assigned to authorized individuals. They can be programmed to provide different levels of access according to each person’s specific needs. PIN codes are personal numerical combinations that must be entered on a keypad to open a door. Biometric recognition systems, on the other hand, use unique physical characteristics such as fingerprints, facial recognition or iris recognition to identify individuals and grant them access.
In addition to these devices, access control systems can also be equipped with surveillance cameras, motion sensors and intercom systems. These additional components enhance security by enabling real-time monitoring, intrusion detection and communication between people inside and outside the building.
The advantages of building access control are numerous. Firstly, it prevents unauthorized intrusion by restricting access to sensitive areas. This ensures that only authorized persons, such as employees, residents or pre-registered visitors, can enter the building.
What’s more, by keeping a record of entries and exits, access control systems can provide valuable information for security management, identifying who is in the building at any given time.
Building access control is particularly important in sensitive environments such as companies, government institutions, hospitals or data centers. In these contexts, protecting assets, confidential information and people is an absolute priority.
In conclusion, building access control is an effective way of enhancing the security and protection of facilities. Through a combination of physical devices and advanced technologies, it regulates access to sensitive areas, prevents unauthorized intrusion and provides valuable information for security management.
What is access control? It is in fact this