Contrôle d’accès
Les solutions d’accès sont utilisée pour gérer l’entrée et la sortie et la présences des personnes dans un bâtiment, sur un site ou un espace restreint. Ces systèmes sont mis en place pour des questions de sécurité, contrôler le nombre de personne dans un espace, de confidentialité, de gestion des ressources et aussi combinés à de la gestion des pointages et des horaires.
Nos solutions de gestion des accès, contrôle d'accès :
ZBioCVSecurity ... contrôle d'accès - module visiteurs
Gestion et accès des visiteurs
CVSecurity fournit une plate-forme de sécurité Web complète avec l’adoption de la biométrie hybride et la technologie de vision par ordinateur. Il contient plusieurs modules :
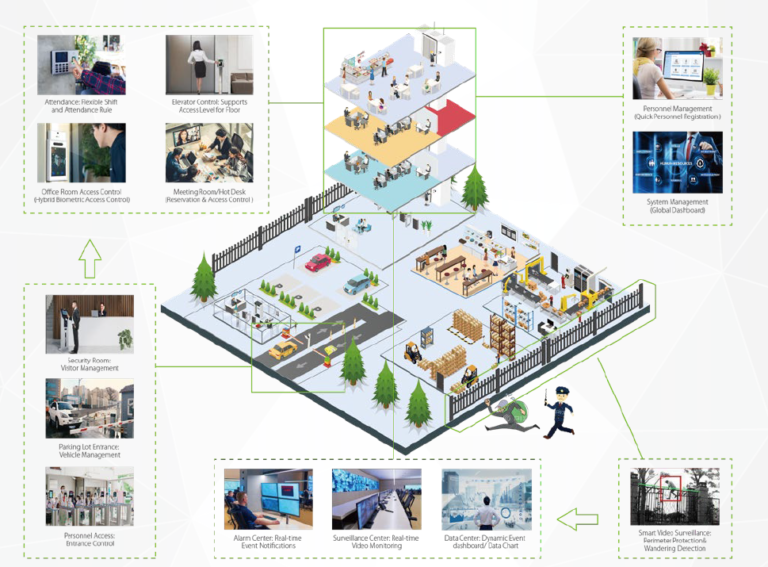
Personnel, Temps et présences, Contrôle d’accès, Visiteur, gestion, de parking, contrôle d’ascenseur, Face Kiosk, gestion vidéo, patrouille de garde, analyse vidéo intelligente, gestion des casiers, alarme d’intrusion, centre de service et autre sous-système intelligent.
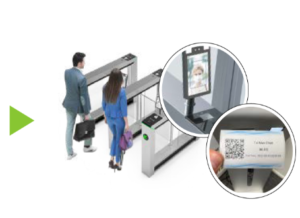
- Prise en charge de la prise de photos des visiteurs
- Prend en charge la déconnexion automatique du compte visiteur. Quand un visiteur ne sort pas normalement, le système conservera les données.
Lorsque la visite du visiteur expire, le système réinitialisera automatiquement les données du visiteur.
- Contrôle d’accès individualisé par visiteurs avec accès aux zones définies, étages par ascenseur etc.
- Différentes méthodes d’authentification comme reconnaissance faciale, empreintes digitales, cartes biométriques, mots de passe et QR codes.
- Possibilité de vérifier le dernier lieu de visite du visiteur, son historique et pop-ups chronométrés ou visiteurs non enregistrés.
et bien plus … démo :
=> https://www.youtube.com/watch?v=9DWCMPLn_JM
Solution complète hardware + software de gestion des accès
La gestion complète des accès est cruciale pour garantir la sécurité et la confidentialité des données au sein d’une organisation. Elle englobe l’ensemble des processus permettant d’administrer, de contrôler et de surveiller les autorisations des utilisateurs.

Cette approche commence par l’identification précise des utilisateurs et de leurs rôles au sein du système. Chaque individu se voit attribuer des droits d’accès en fonction de ses responsabilités, assurant ainsi une répartition appropriée des permissions.
La mise en œuvre d’une gestion complète des accès implique également la surveillance continue des activités des utilisateurs. Des outils de suivi sont déployés pour détecter toute anomalie ou activité suspecte, permettant ainsi une réaction rapide en cas de menace potentielle.
En parallèle, la gestion des accès doit être agile et évolutive. Les autorisations peuvent être ajustées en temps réel pour refléter les changements organisationnels, les promotions, ou encore les départs d’employés, assurant ainsi une sécurité constante.
demandez la doc => https://horomeca.com/contact/
Lecteur XPASS Slim 2
Le lecteur de contrôle d’accès, de gestion et de monitoring d’accès, installé aux portes le “XPASS Slim 2” est une unité, lecteur de badges, de contrôle d’accès muni d’une IP avec un très haut niveau de sécurité.
Il résiste à des températures de -35 ° C à + 65 ° C, il est donc adapté aux installations en extérieur, pour tout type de temps et sur tous les continents.
Il est équipé d’un Microprocesseur 32 bits, Mifare, Felica, Desfire (CSN) (533 Mhz), 12 V CC et est “IP65” (waterproof).
Logiciel SYnergy Workforce | Module "accès"
Le “module” gestion d’accès, groupe solutions d’accès, de notre logiciel “Synergy WorkForce Management” (HorioWeb), contrôle l’accès aux portes, permet d’accéder à certaines zones à des heures prédéfinies et n’y rester qu’un certain laps de temps.
Vous pouvez contrôler les entrées et sorties des employés et des visiteurs à tout moment, d’éditer des rapports quotidiens, hebdomadaires, mensuels ou annuels.
Le système est totalement flexible et s’adapte aux évolutions de l’entreprise.
QR600
La série QR600 de lecteurs de codes QR
… et de cartes RFID est composée de métal, classé IP65 (étanche à l’eau et à la poussière). Le lecteur QR prend en charge la reconnaissance dynamique du code QR avec l’application mobile BioSecurity et la série Atlas.
Caractéristiques – Boîtier métallique robuste et étanche
Clavier (QR600-HK et QR600-VK) – IP65 étanche – Compatible avec les solutions de codes QR dynamiques – Code QR, PDF417, Data Matrix, MicroPDF417, Aztèque – Communication : Wiegand et RS485 – Lecture de cartes 125 kHz, IC 13,56 MHz (notamment Ultralight), Mifare (S50/S70), CPU, NFC (carte analogique), Desfire EV1, NTag.
Bio Entry
Certifié IP67,
le BioEntry
est protégé contre l’humidité, la poussière et les liquides.
Certifié IK08, il résiste à toutes les tentatives de vandalisation.
Il sécurise l’extérieur des bâtiments.
Il est biométrique et a Proximity EM, Hid Prox, Mifare, Felica, NFfc, Desfire, Iclass.
Lecteur de haute technologie répandue de par le monde et compatible avec les solutions et logiciels de contrôle d’accès mais aussi de gestion de temps, des présences et des pointages.
Contrôleurs Atlas
Cet appareil a un logiciel intégré dans les contrôleurs, une gestion conviviale et complète de n’importe où vous êtes via internet. Toutes vos portes sont sécurisées avec des appareils WiFi qui peuvent chacun contrôler jusqu’à plusieurs portes. Nos contrôle d’accès peuvent être équipé de lecteurs de badges, RFID, MiFare ou HID, lecteurs d’empreintes digitales et reconnaissance faciale.
 Le contrôle d’accès est un élément essentiel de la sécurité dans de nombreux environnements, qu’il s’agisse de bâtiments, de réseaux informatiques ou de systèmes d’information sensibles. Il fait référence aux mesures prises pour réguler et surveiller l’entrée et la sortie des personnes, des véhicules ou des données dans un espace ou un système donné.
Le contrôle d’accès est un élément essentiel de la sécurité dans de nombreux environnements, qu’il s’agisse de bâtiments, de réseaux informatiques ou de systèmes d’information sensibles. Il fait référence aux mesures prises pour réguler et surveiller l’entrée et la sortie des personnes, des véhicules ou des données dans un espace ou un système donné.
Dans le contexte des bâtiments, le contrôle d’accès vise à protéger les installations et les occupants contre les intrusions non autorisées. Il peut prendre la forme de dispositifs physiques tels que des serrures, des lecteurs de cartes ou des systèmes de reconnaissance biométrique. Ces mesures permettent de restreindre l’accès à des zones spécifiques, de suivre les mouvements des individus et de garantir que seules les personnes autorisées puissent entrer dans les zones sensibles.
Le contrôle d’accès aux bâtiments est un aspect essentiel de la sécurité et de la protection des installations. Il s’agit d’un ensemble de mesures et de dispositifs mis en place pour réguler et surveiller l’entrée et la sortie des personnes dans un espace donné, en veillant à ce que seules les personnes autorisées puissent accéder aux zones sensibles.
Les systèmes de contrôle d’accès aux bâtiments peuvent être de différentes natures. L’un des moyens les plus couramment utilisés est l’installation de serrures et de clés, qui permettent de limiter l’accès aux portes et aux zones spécifiques. Cependant, ces systèmes traditionnels ont évolué pour inclure des technologies plus avancées telles que les cartes d’accès, les codes PIN et les systèmes de reconnaissance biométrique.
Les cartes d’accès sont des dispositifs électroniques qui sont attribués aux individus autorisés. Elles peuvent être programmées pour fournir différents niveaux d’accès en fonction des besoins spécifiques de chaque personne. Les codes PIN sont des combinaisons numériques personnelles qui doivent être saisies sur un clavier pour permettre l’ouverture d’une porte. Les systèmes de reconnaissance biométrique, quant à eux, utilisent des caractéristiques physiques uniques telles que les empreintes digitales, la reconnaissance faciale ou la reconnaissance de l’iris pour identifier les individus et leur accorder l’accès.
Outre ces dispositifs, les systèmes de contrôle d’accès peuvent également être équipés de caméras de surveillance, de capteurs de mouvement et de dispositifs d’interphonie. Ces composants supplémentaires renforcent la sécurité en permettant la surveillance en temps réel, la détection des intrusions et la communication entre les personnes à l’intérieur et à l’extérieur du bâtiment.
Les avantages du contrôle d’accès aux bâtiments sont nombreux. Tout d’abord, il permet de prévenir les intrusions non autorisées en limitant l’accès aux zones sensibles. Cela garantit que seules les personnes autorisées, telles que les employés, les résidents ou les visiteurs préalablement enregistrés, puissent entrer dans le bâtiment.
De plus, en maintenant un registre des entrées et des sorties, les systèmes de contrôle d’accès peuvent fournir des informations précieuses pour la gestion de la sécurité, en identifiant les personnes présentes dans le bâtiment à tout moment.
Le contrôle d’accès aux bâtiments est particulièrement important dans les environnements sensibles tels que les entreprises, les institutions gouvernementales, les hôpitaux ou les centres de données. Dans ces contextes, la protection des biens, des informations confidentielles et des personnes est une priorité absolue.
En conclusion, le contrôle d’accès aux bâtiments est un moyen efficace de renforcer la sécurité et la protection des installations. Grâce à une combinaison de dispositifs physiques et de technologies avancées, il permet de réguler l’accès aux zones sensibles, de prévenir les intrusions non autorisées et de fournir des informations précieuses pour la gestion de la sécurité.
Le contrôle d’accès c’est quoi ? C’est en fait ceci